This article provides detailed example of how to provide different user groups with access to different scope of cluster logging/monitoring information using RBAC.
The example covers the following RBAC model:
operations group have access to:audit group have access to:develop and prod spaces (read-only)kublr-ui realm.KublrOperations and KublrAudit groups.user_operations realm role.audit user and add one to the KublrReadOnlyUsers and KublrAudit groups.operations user and add one to KublrReadOnlyUsers and KublrOperations groups.operations user, at Role mapping tab, assign the user_operations role.develop and prod spaces.In Security → Roles, create global roles:
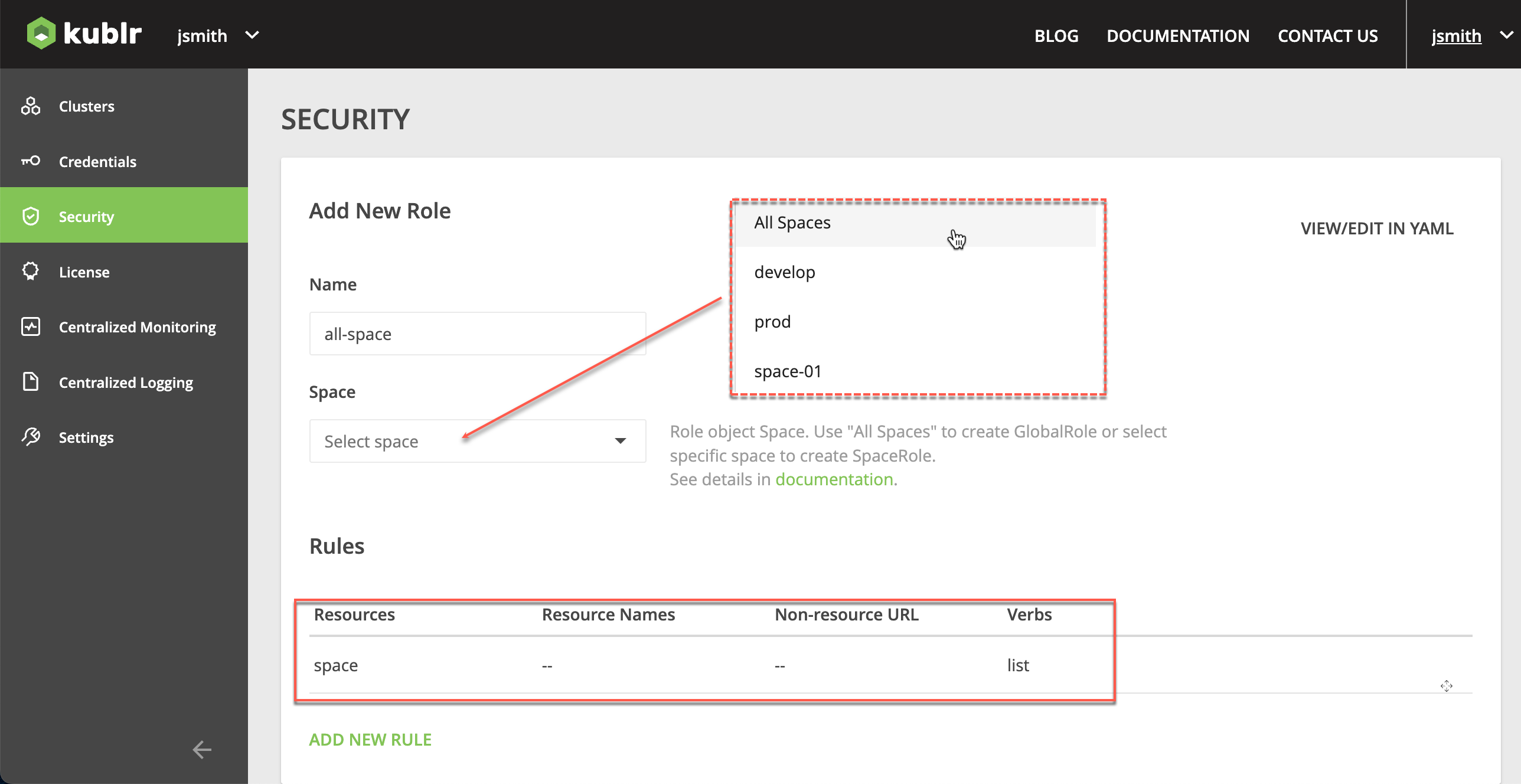
all-space: rule for space, Verbs - “list”
all-clusters: rule for space, cluster, cluster/id, Verbs - “list, get”
cluster-dashboard: rule for cluster/proxy, cluster/admin-dashboard, cluster/dashboard, cluster/admin-proxy, Verbs - “get”
In Security → Role Bindings, create global role bindings:
all-spaces-viewer: bind the all-space role to KublrOperations and KublrAudit groupscluster-dashboard-audit: bind the cluster-dashboard role to KublrAudit groupAnd space role bindings:
operations-dev-space: for space develop, bind all-clusters role KublrOperations and KublrAudit groups
operations-prod-space: for space prod bind all-clusters role to KublrOperations and KublrAudit groups

Login to the cluster with administration config.
Using k9s or kubctl tools search pod kublr-logging-controller-* in Kublr namespace and enter with shell to the kublr-feature-logging container.
To export configuration of Search Guard, execute the /opt/logging-controller/sg_retrieve.sh script.
Go to /tmp folder with the cd /tmp.
Add the following code to the end of the roles.yml file:
sg_user_operations:
exclude_index_permissions:
- actions:
- "*"
index_patterns:
- "*kublr_*_audit*"
- "*kublr_*_kube-system-*"
Add the following code to the end of the roles_mapping.yml file:
sg_user_operations:
backend_roles:
- "user_operations"
To import configuration to Search Guard, execute the /opt/logging-controller/sg_apply.sh script.