Keycloak provides a feature to enable login with various identity providers, including Microsoft Entra ID (previously known as Azure Active Directory, Azure AD). Here are the steps to configure Keycloak to allow login with an account from Microsoft Entra ID.
Prerequisites:
Access https://<kublr-url>/auth.
The Keycloak login page is displayed.
Login into Keycloak using admin login and password.
Get the Keycloak URL from the address bar. This should be something like:https://<kublr-url>/auth/realms/kublr-ui/broker/microsoft/endpoint
In Microsoft Entra ID:
Login to the Azure portal and go to Entra ID.
Select App Registrations and then click New Registration.
Provide a name for your application.
Select the supported account type.
In the Redirect URI section, select Web and input the Keycloak URL.
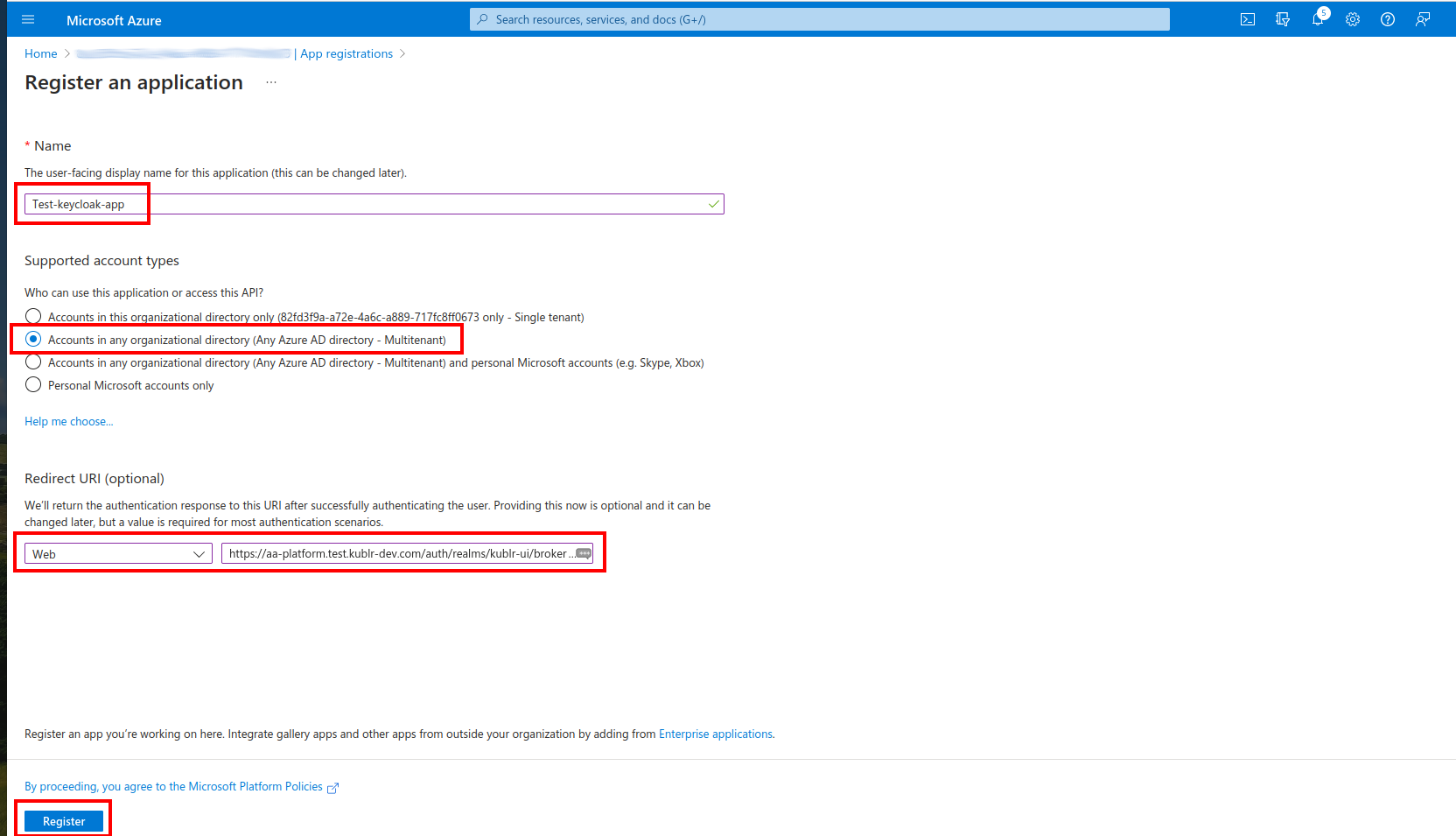
Click Register. The application is created, and its page is displayed.
Copy and save the Application (client) ID and the Directory (tenant) ID.
Go to Certificates & secrets.
In the Client Secrets section, click New Client Secret.
Add a description, select an expiration period, and then click Add.
Copy the client secret value.
In Kublr’s Keycloak:
Access your Kublr’s Keycloak https://<kublr-url>/auth as described in “Prerequisites”.
Select the kublr-ui realm to add Azure AD as an identity provider.
Go to Identity Providers and click Microsoft. The Add Microsoft provider dialog is displayed.
In the Add Microsoft provider dialog, set:
Application (client) ID.value of the client secret.The Redirect URI will be automatically filled and should match the one you set in Azure.
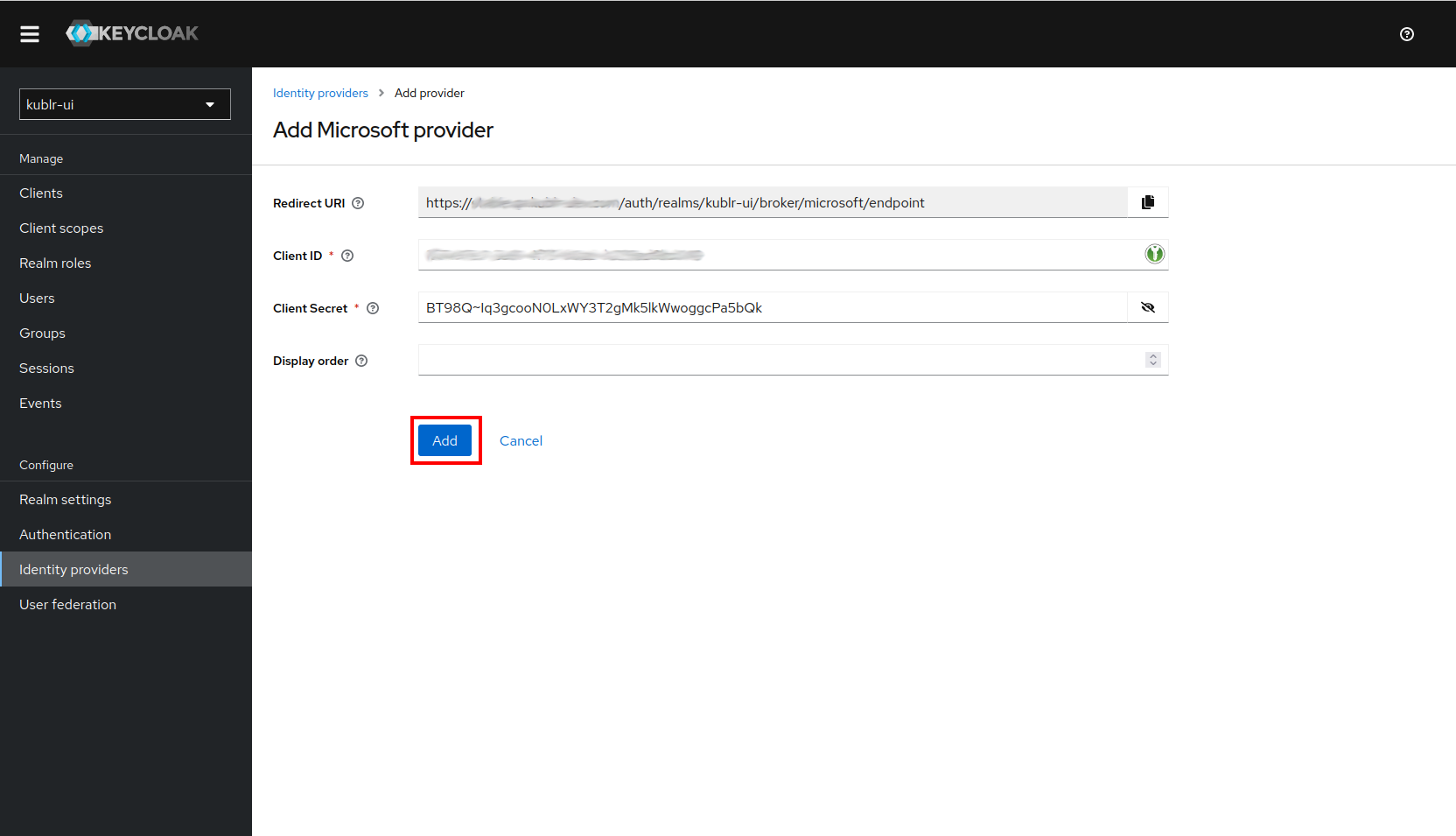
Click Add. Now you can log in to the Kublr via Microsoft.
This documentation: