Kubernetes RBAC Integration
Overview
Kublr provides a convenient UI for Kubernetes RBAC management. This article described how access to certain Kubernetes namespaces
can be restricted using this UI. A common use-case is to provide developers with read-only permissions to your production
environment (aka namespace in Kubernetes).
Setup
- Open the Kublr Platform (or, if you don’t have one yet, create one. Please refer to Kublr installation manuals for instructions).
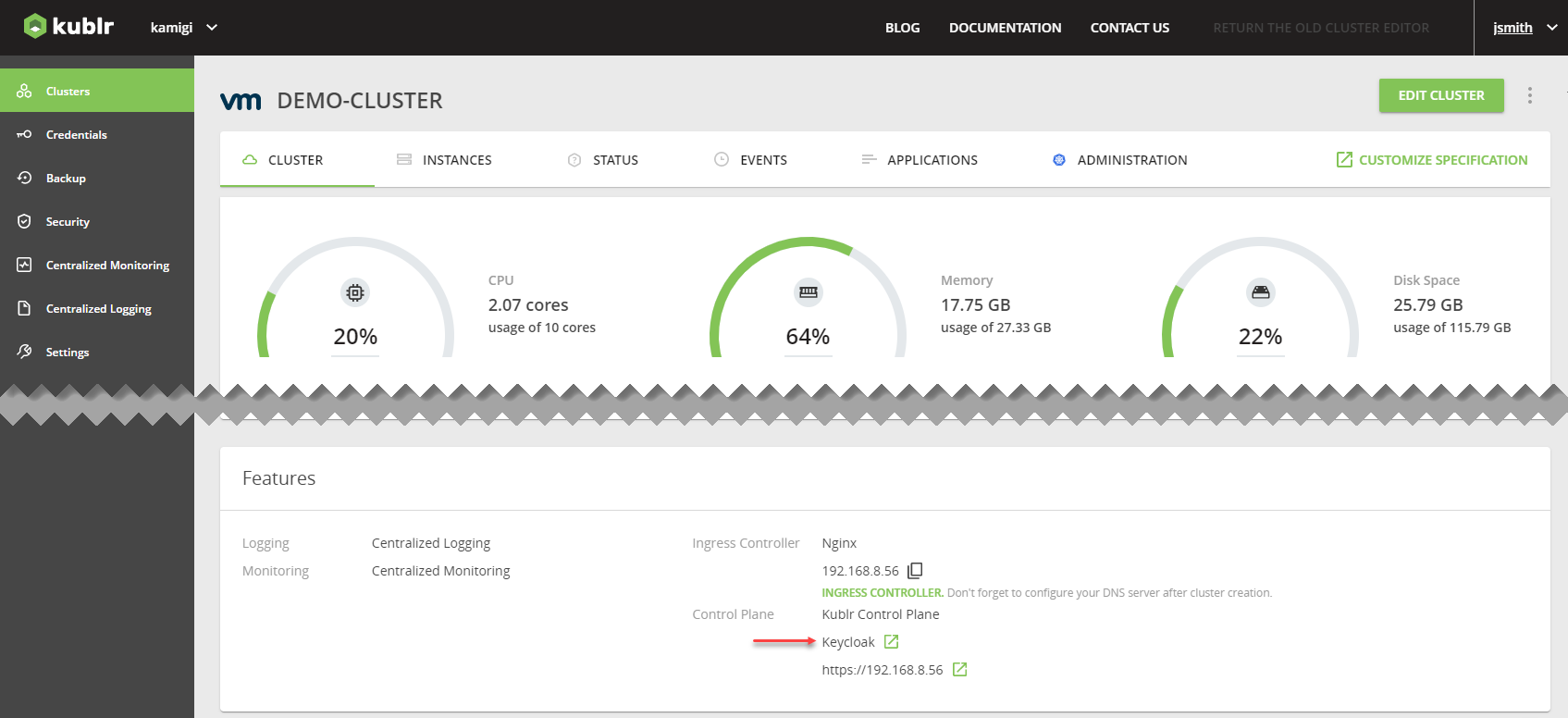
- Go to Keycloak.
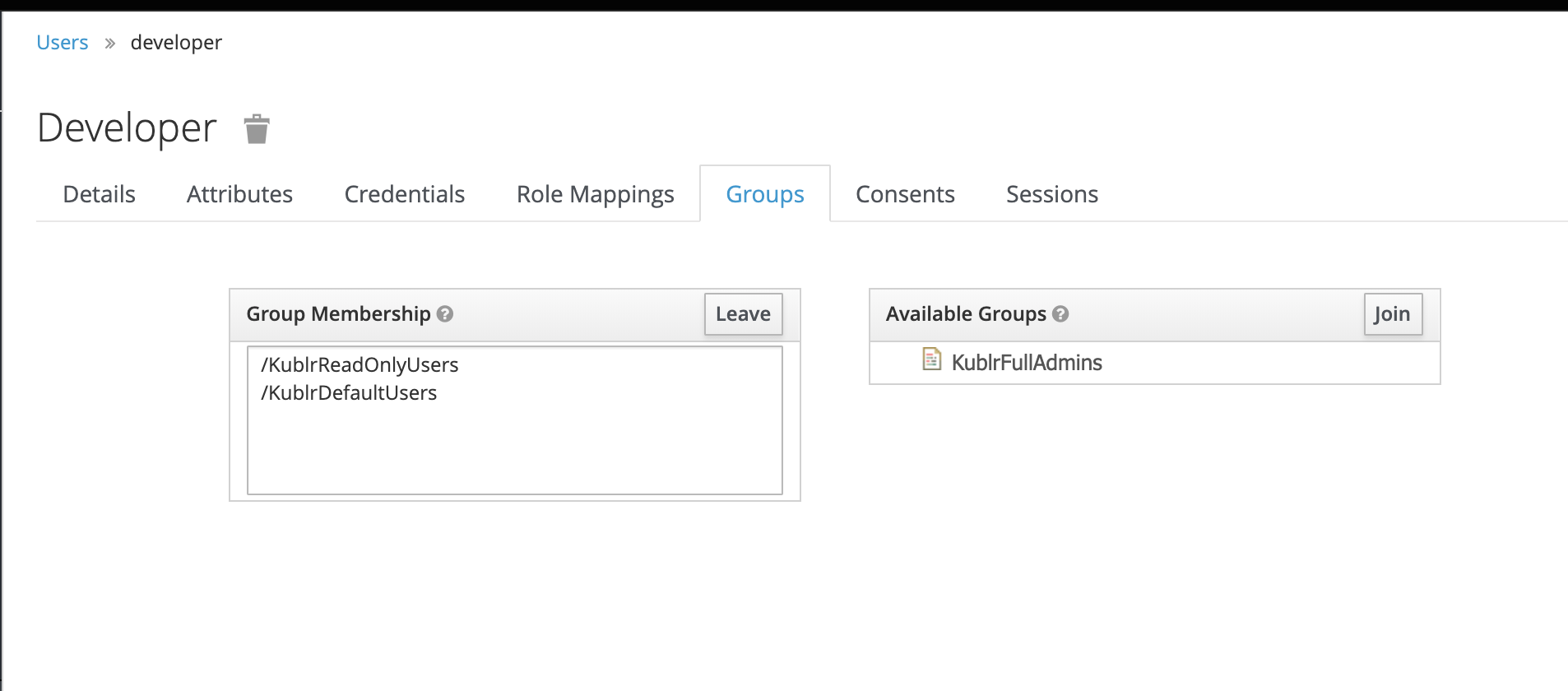
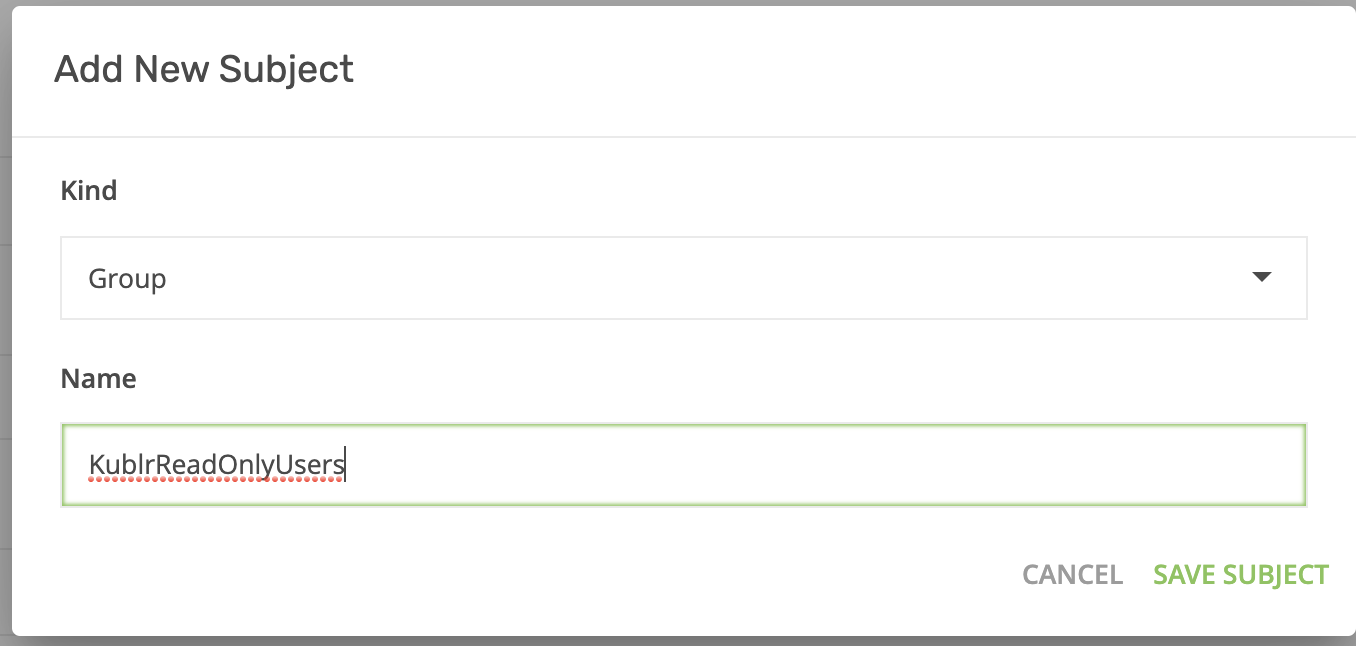
- In the main Keycloak screen, go to “User” (left menu) and create a new user named “developer” (disable temporary, set email verified). Set a password and add the user to the read-only group named “KublrReadOnlyUsers”.
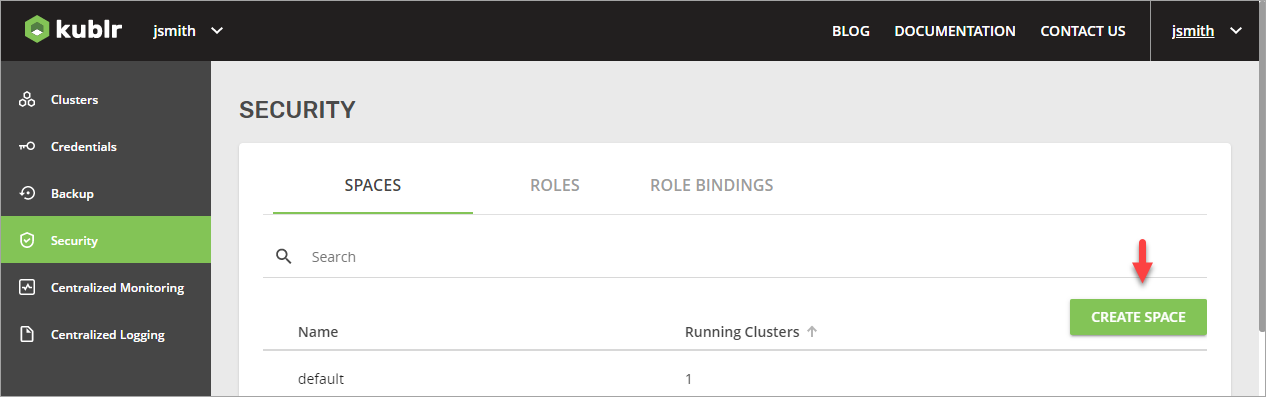
- Go to the Kublr UI, create a space, and name it “production”.
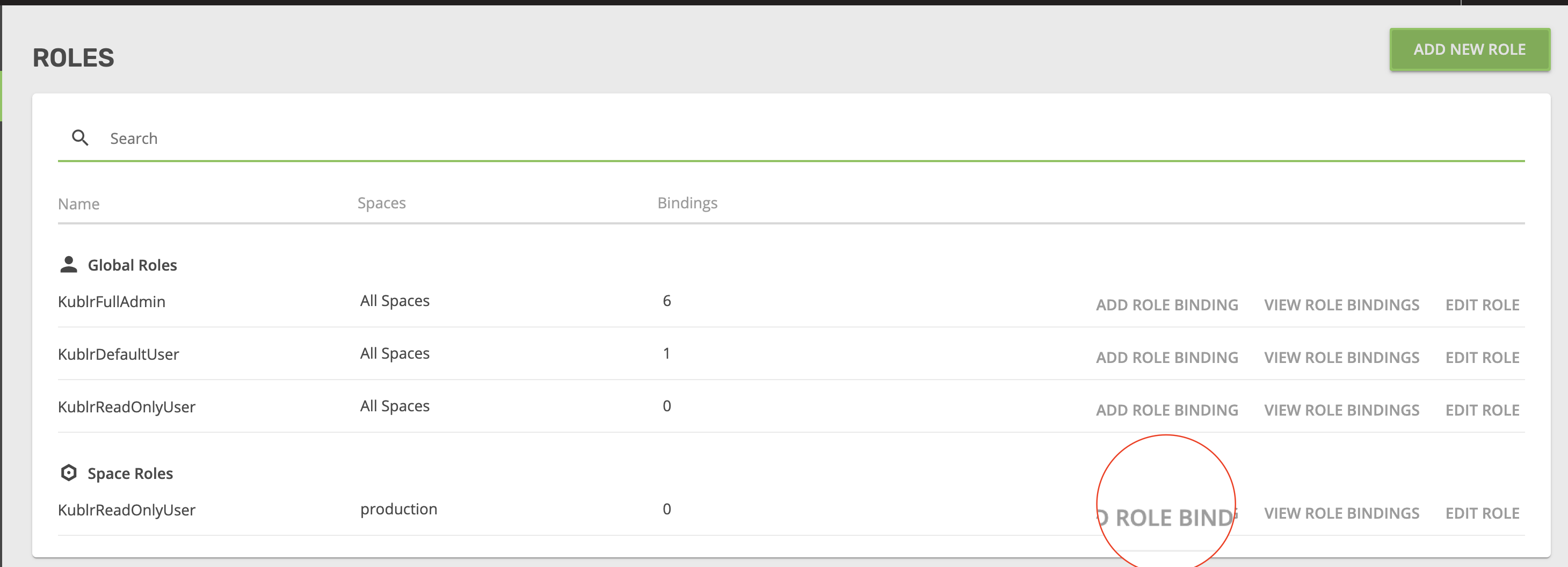
- Now, go to the Roles tab and add a new role.
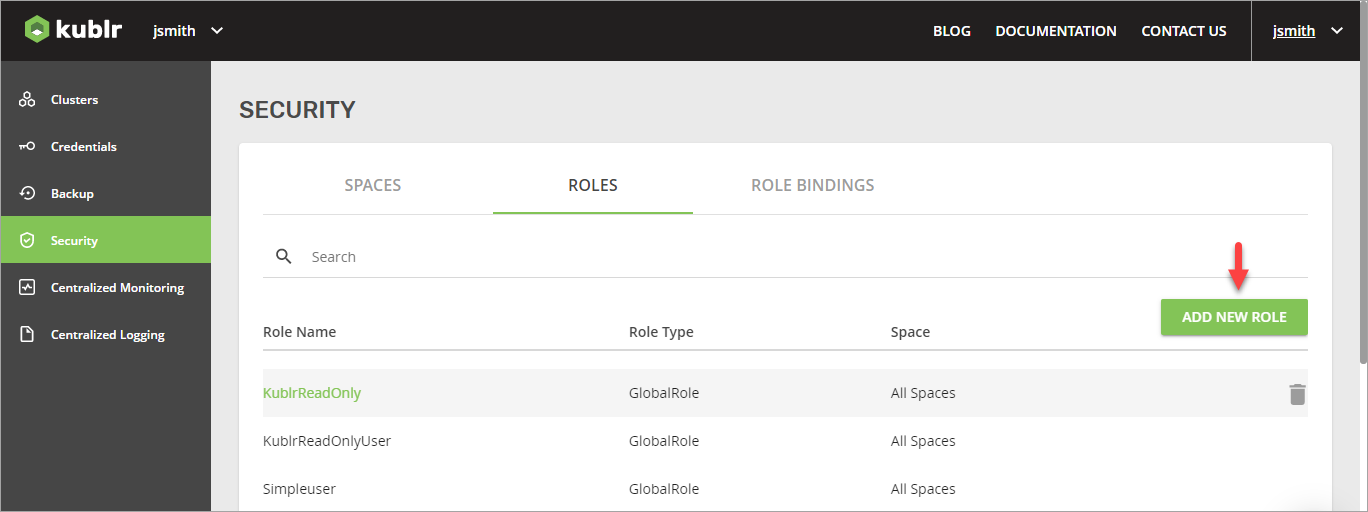
- Specify the role parameters, as shown in these screenshots.
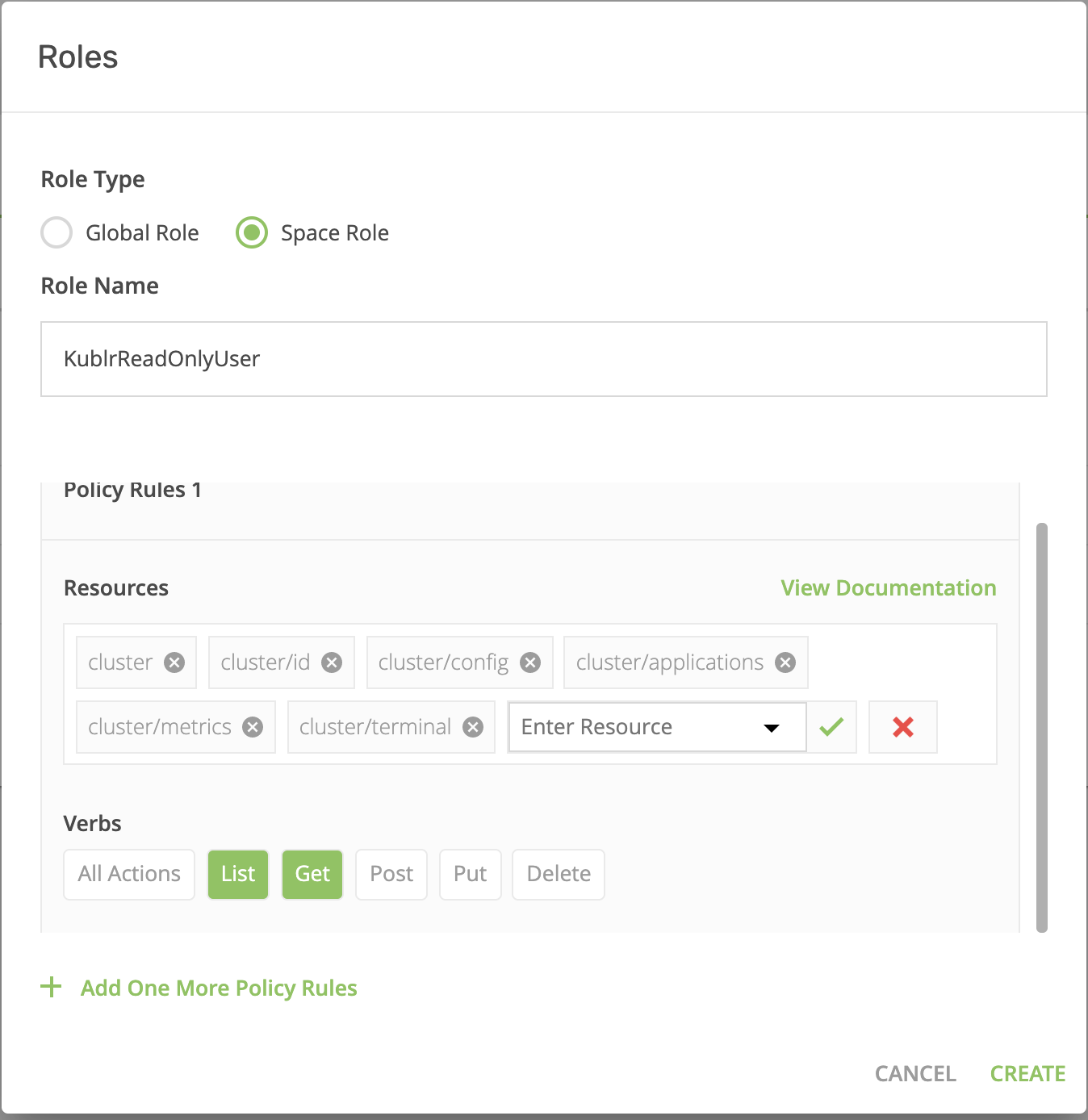
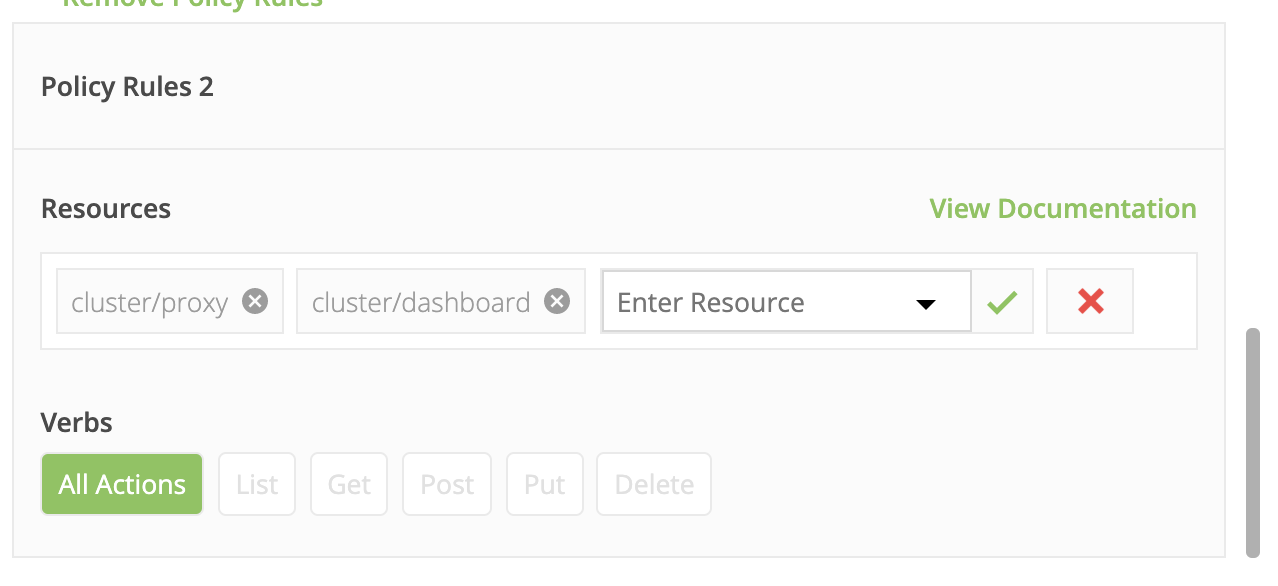
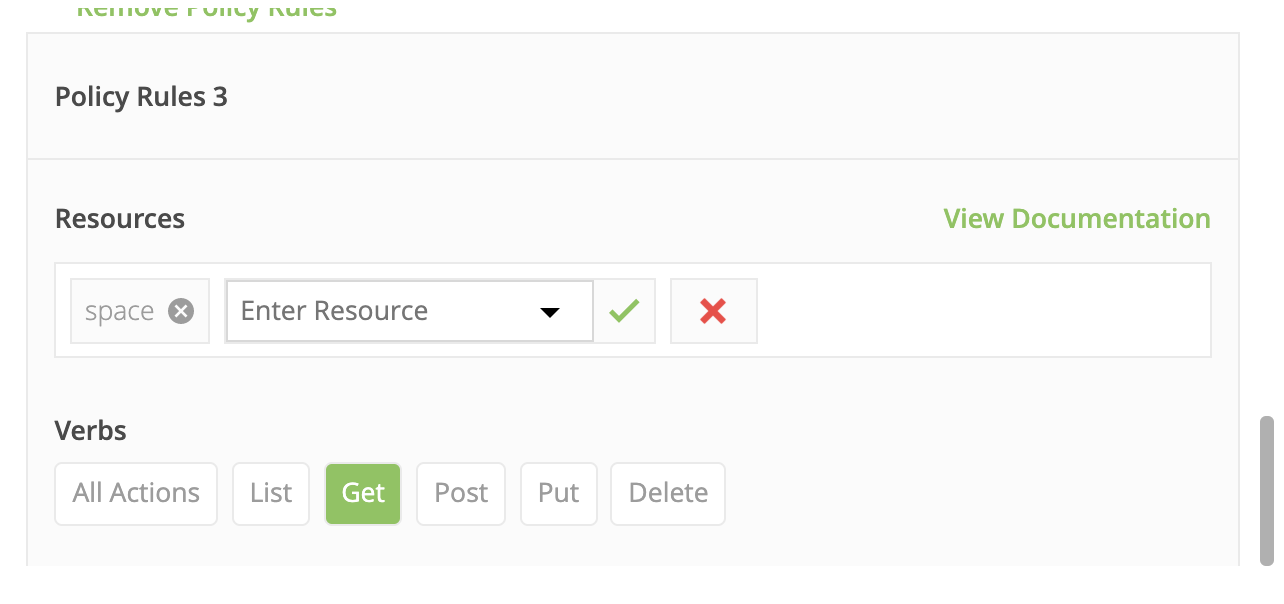
- On “KublrReadOnlyUsers,” click “add role binging” to assign the group (e.g., all users named “developer”) to the “production” space and grant them access. These users can now observe clusters in prod without being able to execute any actions. You can find more details about Kublr spaces here Kublr RBAC UI
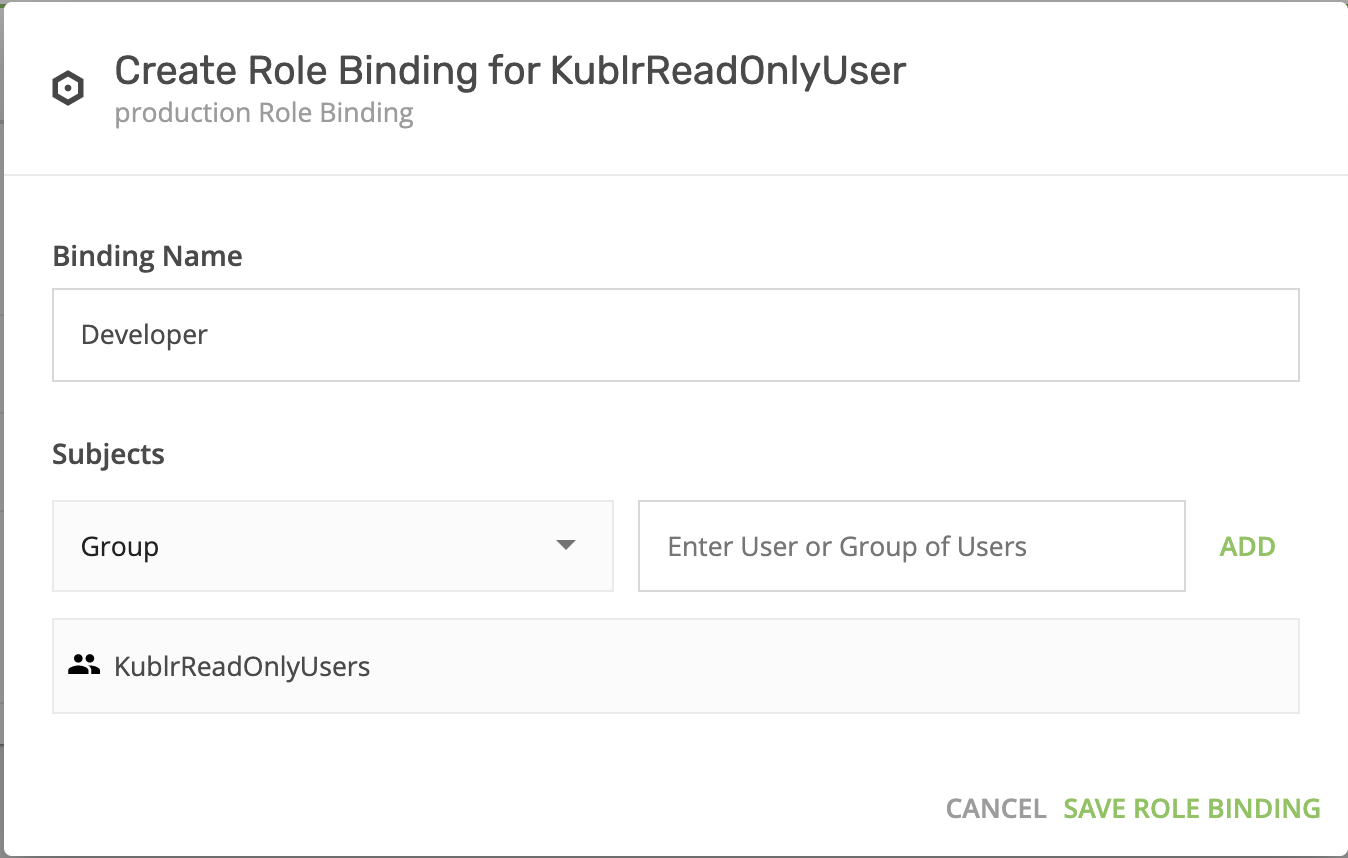
- Now, switch to the “production” space (top-left menu) and create a cluster (refer to installation manuals for more information).
- Once you created a cluster in the “production” space, go to the cluster overview page and click on the “Open Web Console” link. This will open a terminal with the embedded kubectl. Use it to create a Kubernetes namespace and name it “production”.
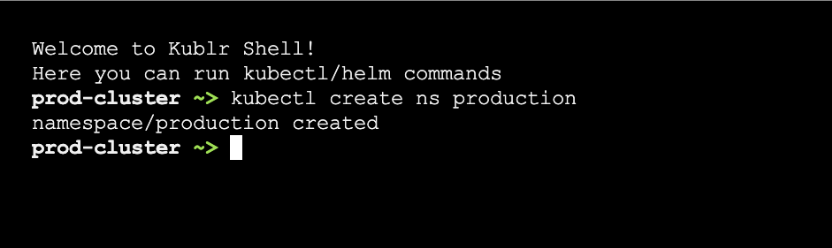
- In the newly created cluster, go to the
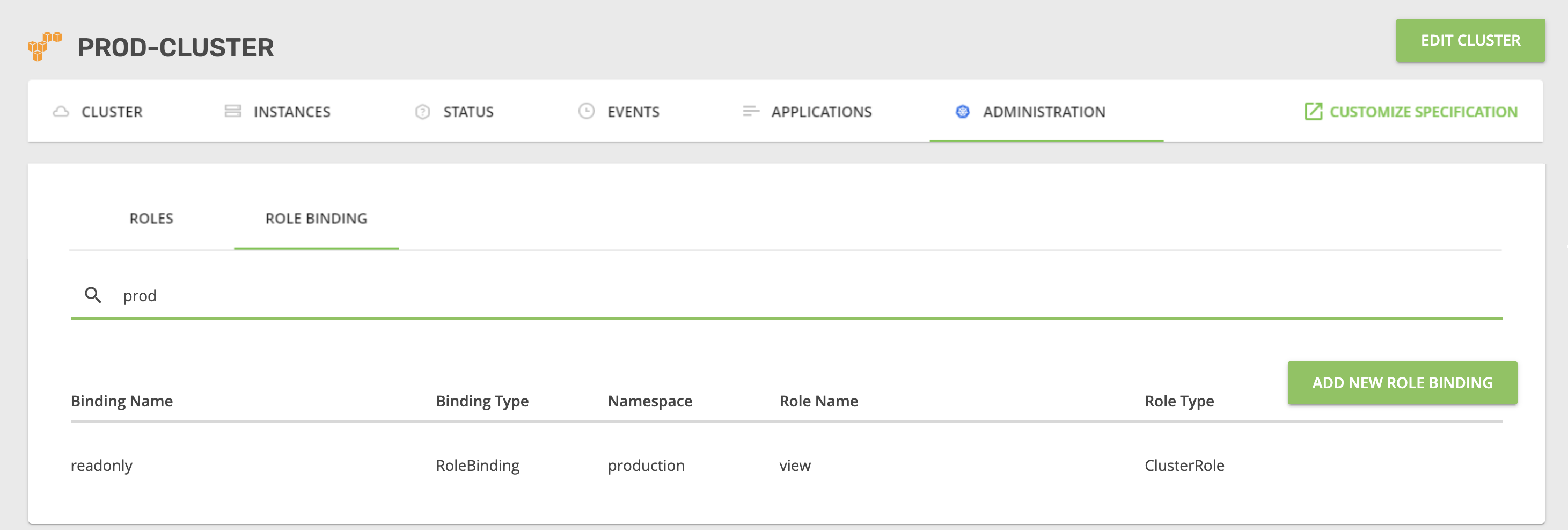
ADMINISTRATION tab, which will allow you to manage Kubernetes RBAC. - Use the ROLE BINDING sub-tab.
- Click ADD NEW ROLE BINDING.
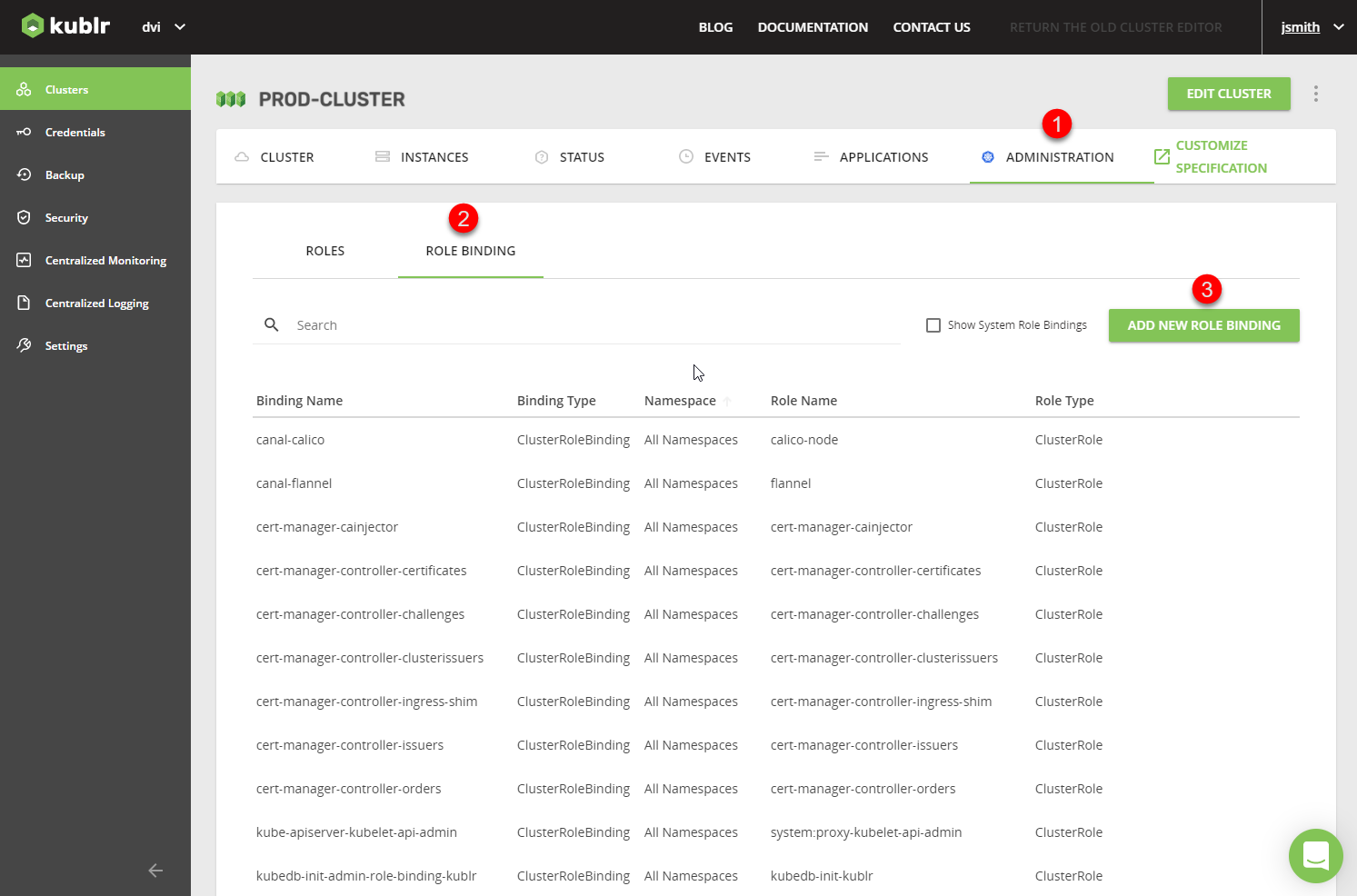
- Fill in the parameters (namespace - production, select role - view), add a subject for the “KublrReadOnlyUsers” group, and assign it a Kubernetes role in Keycloak (and all users in the group). That way, all “developer” users will have a “view role” in the “production” namespace of the cluster.
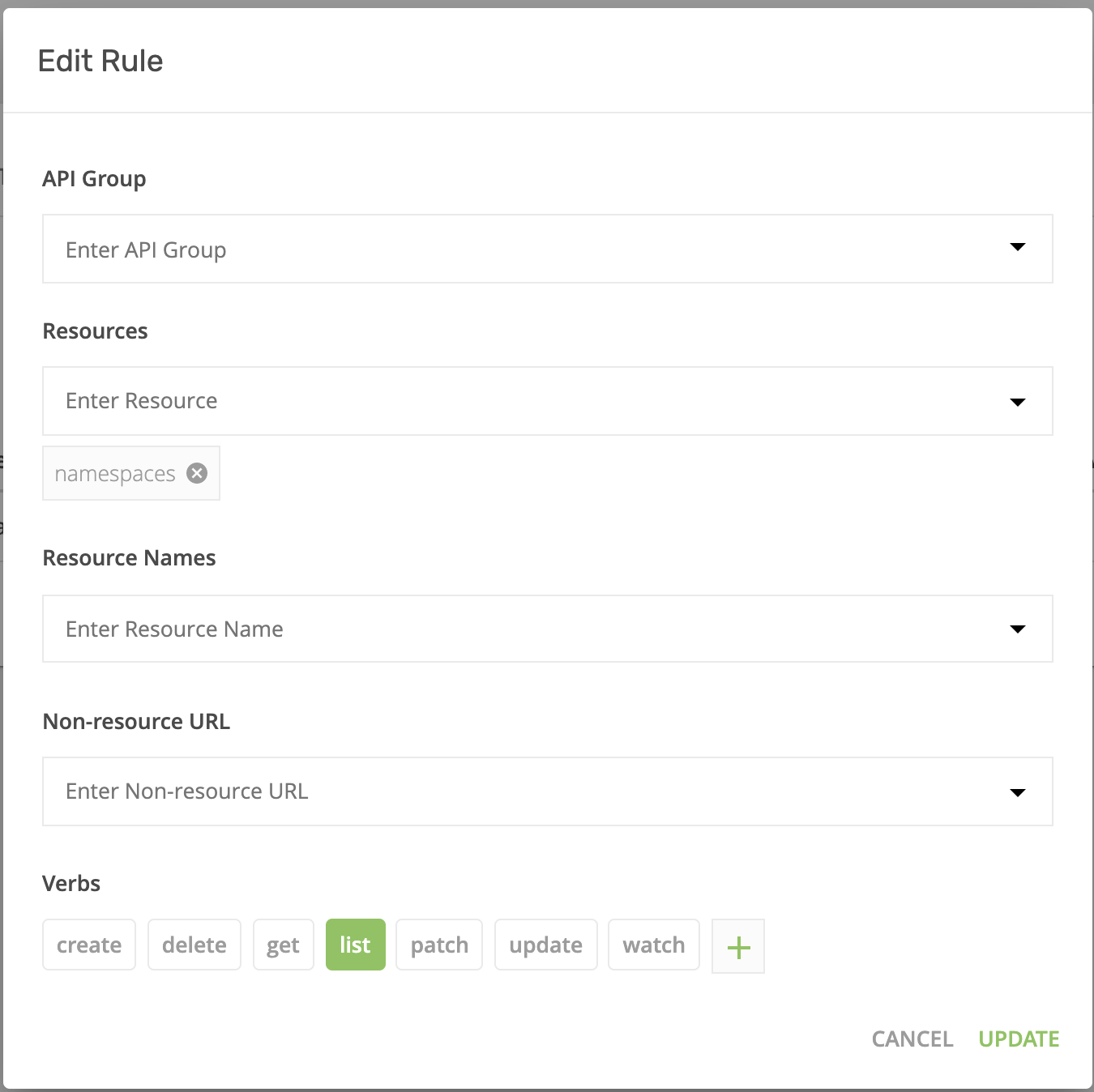
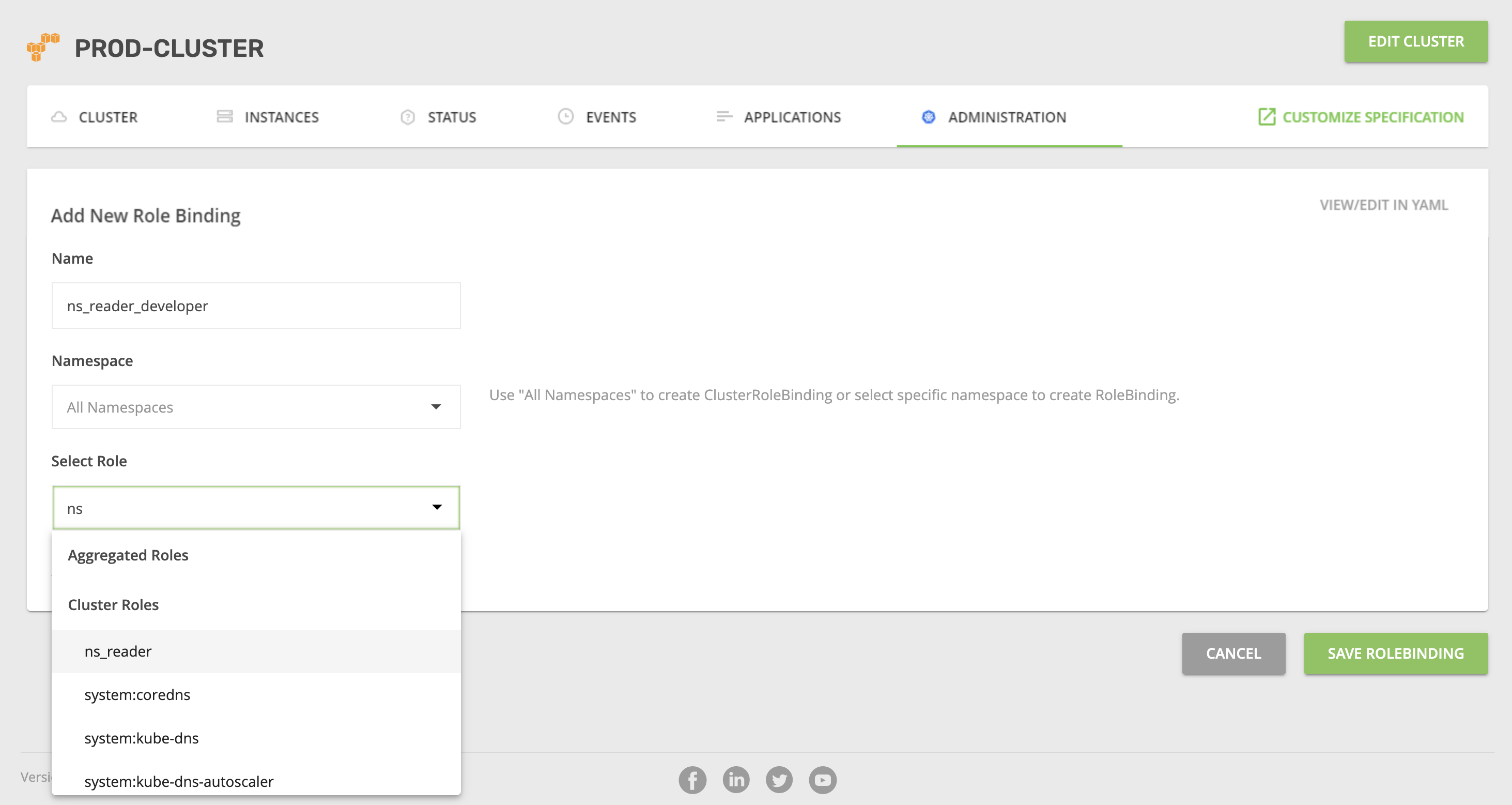
- Now you’ll need to create an additional Kubernetes role binding to allow users to see all namespaces in the Kubernetes cluster, including those they don’t have access to. Go to “Roles” and create a new role. Then, assign that role to the subject “KublrReadOnlyUsers”
Your setup is ready. Logout as admin and in again as “developer”. Go to the cluster overview page and click on the “Open Dashboard” link.
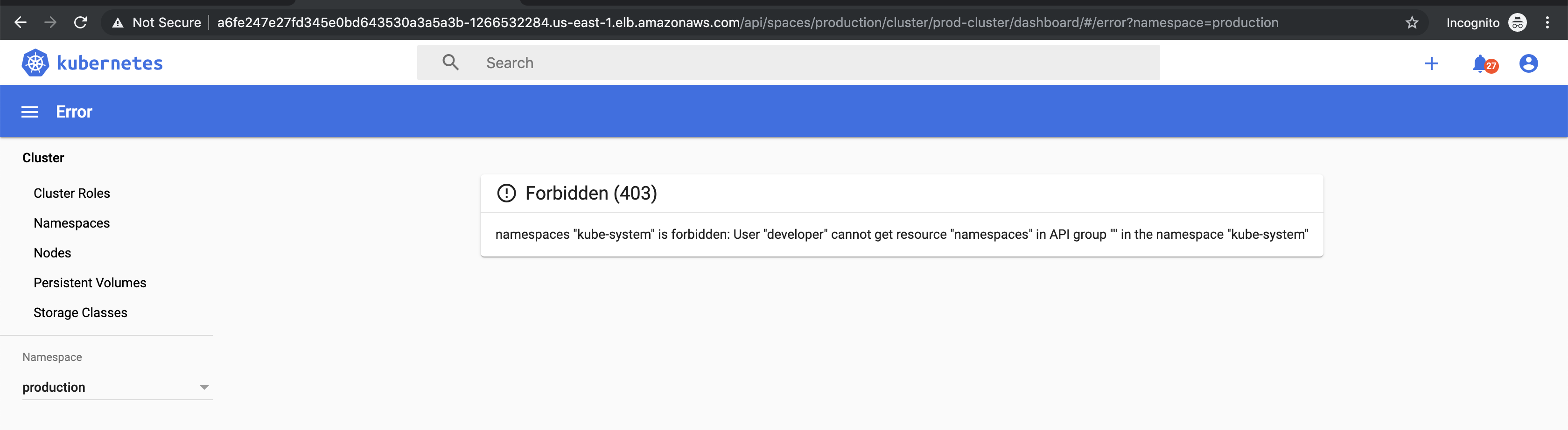
You’ll see a list of all resources under the “production” namespace. But if you try to delete something, you’ll get this message:
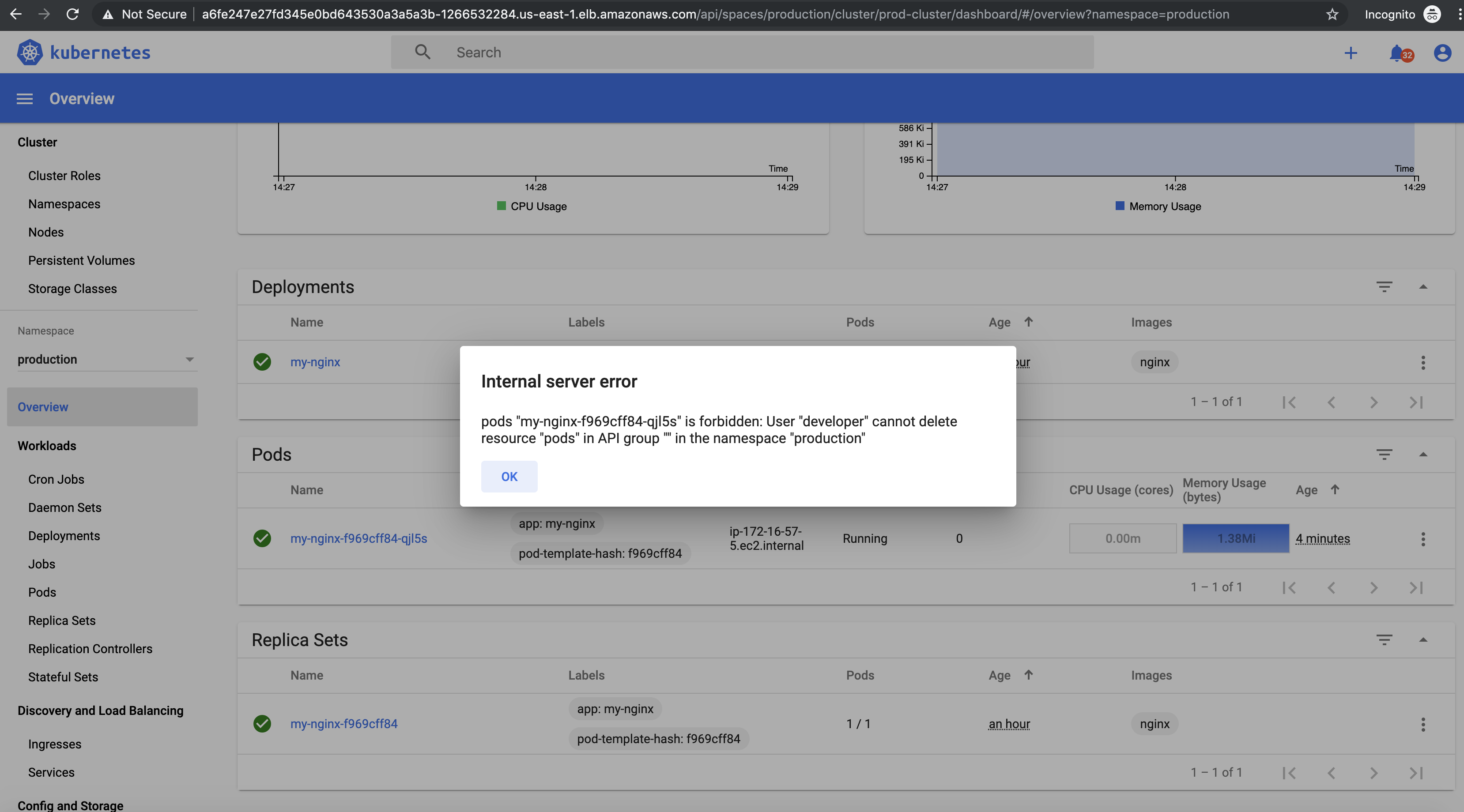
Additionally, you won’t be able to list resources in any other namespace.